Connecting Mosaic with Google SAML
Initial Setup with Google SAML
- Create a Group on Google Workspace.
- Navigate to Groups and select Create Group.
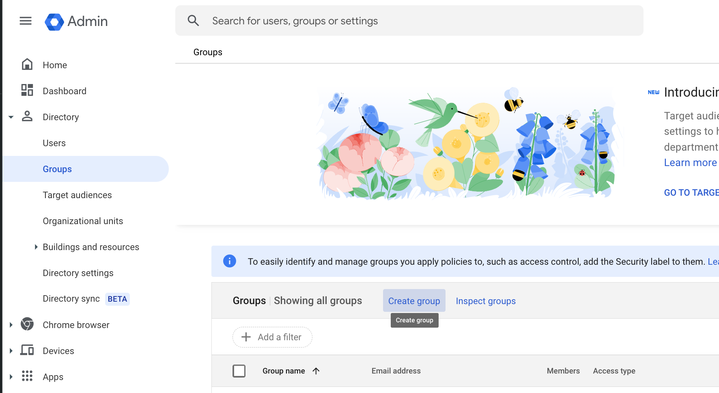
- Then fill out the fields however you'd like. Making sure to select the
Securitybox at the bottom.
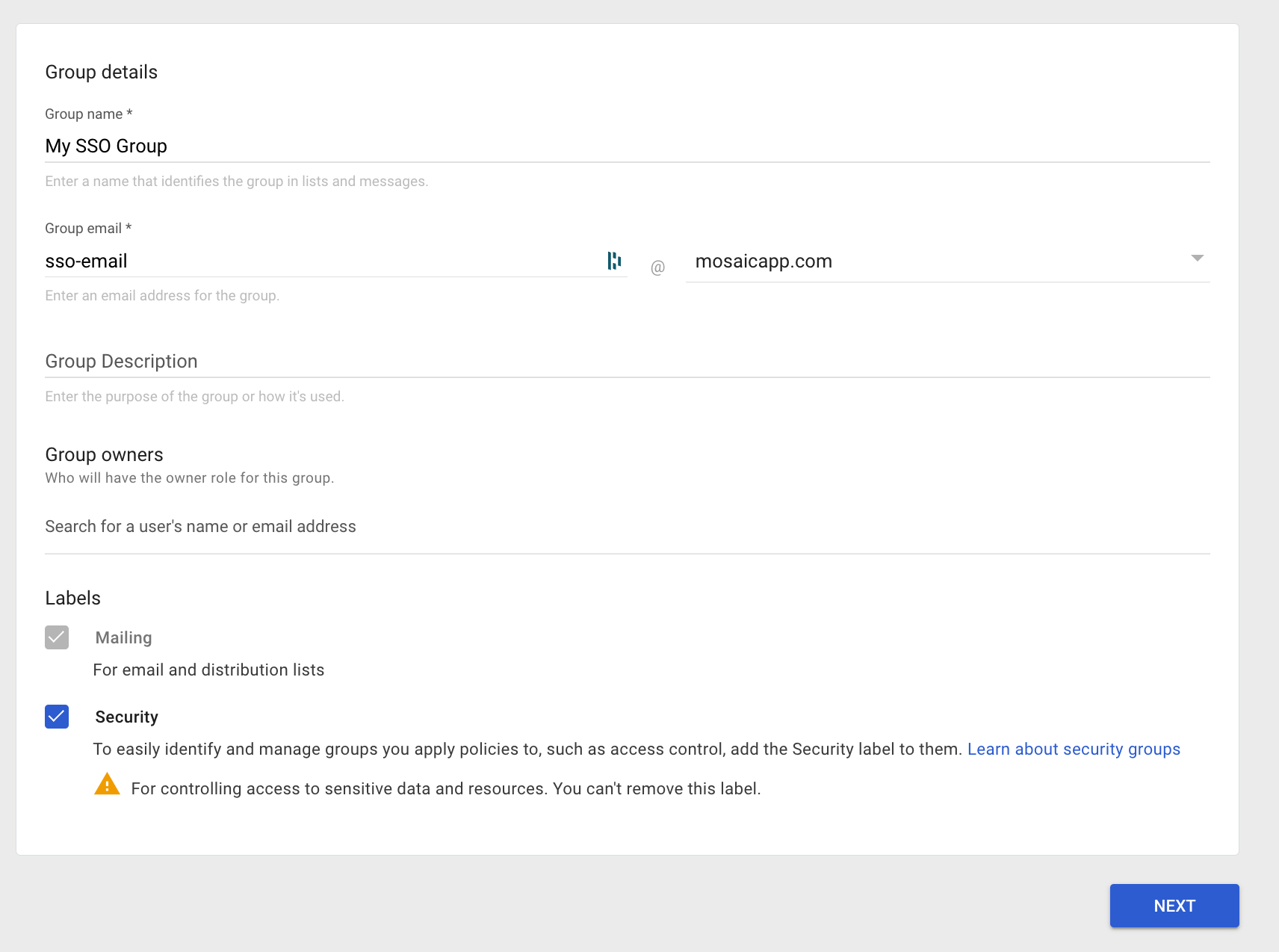
- You can set the Access type to however you'd like to manage the
Group, then add Users to theGroup.
- Navigate to Apps → Web and mobile apps
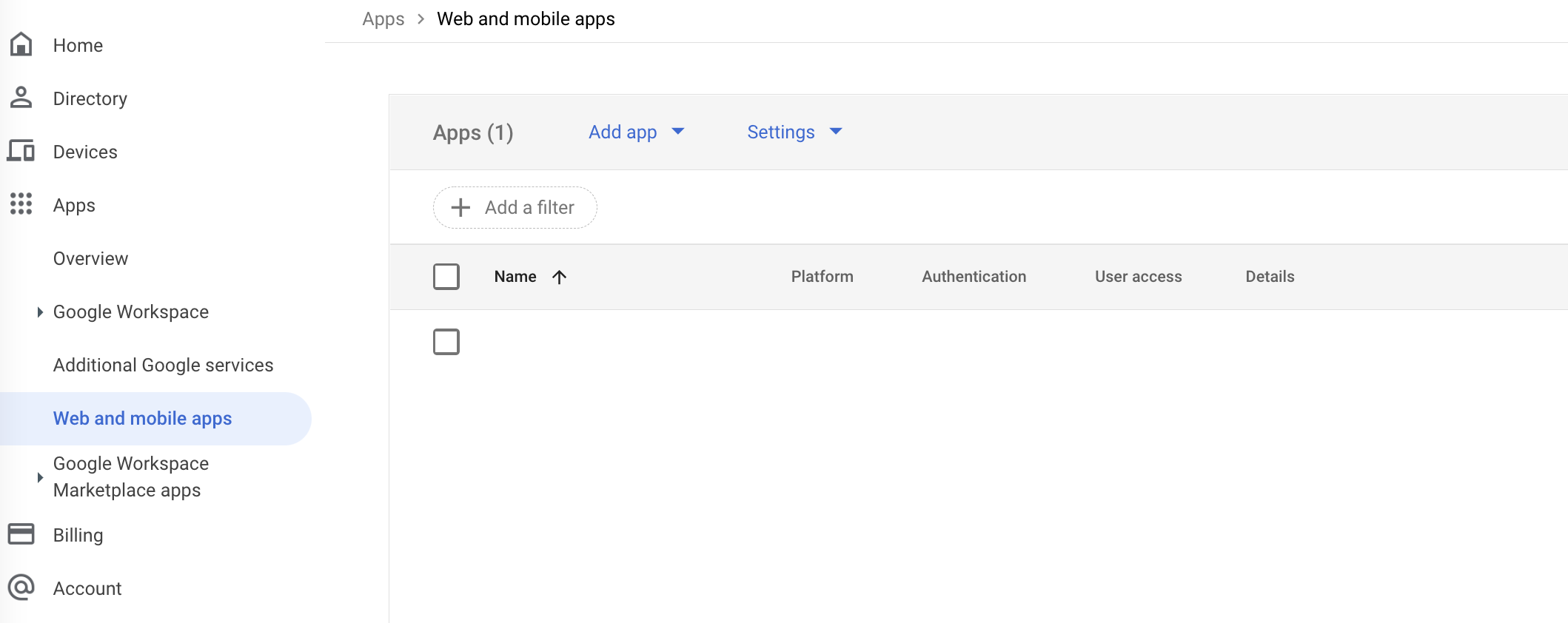
- Click on App app → Add custom SAML app
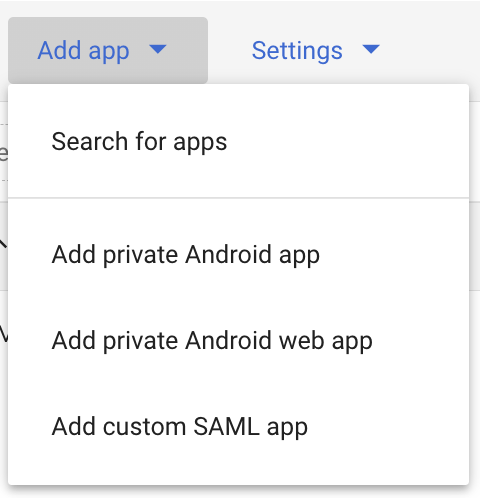
- Enter a custom App name. You can also add an optional description and an optional app icon.
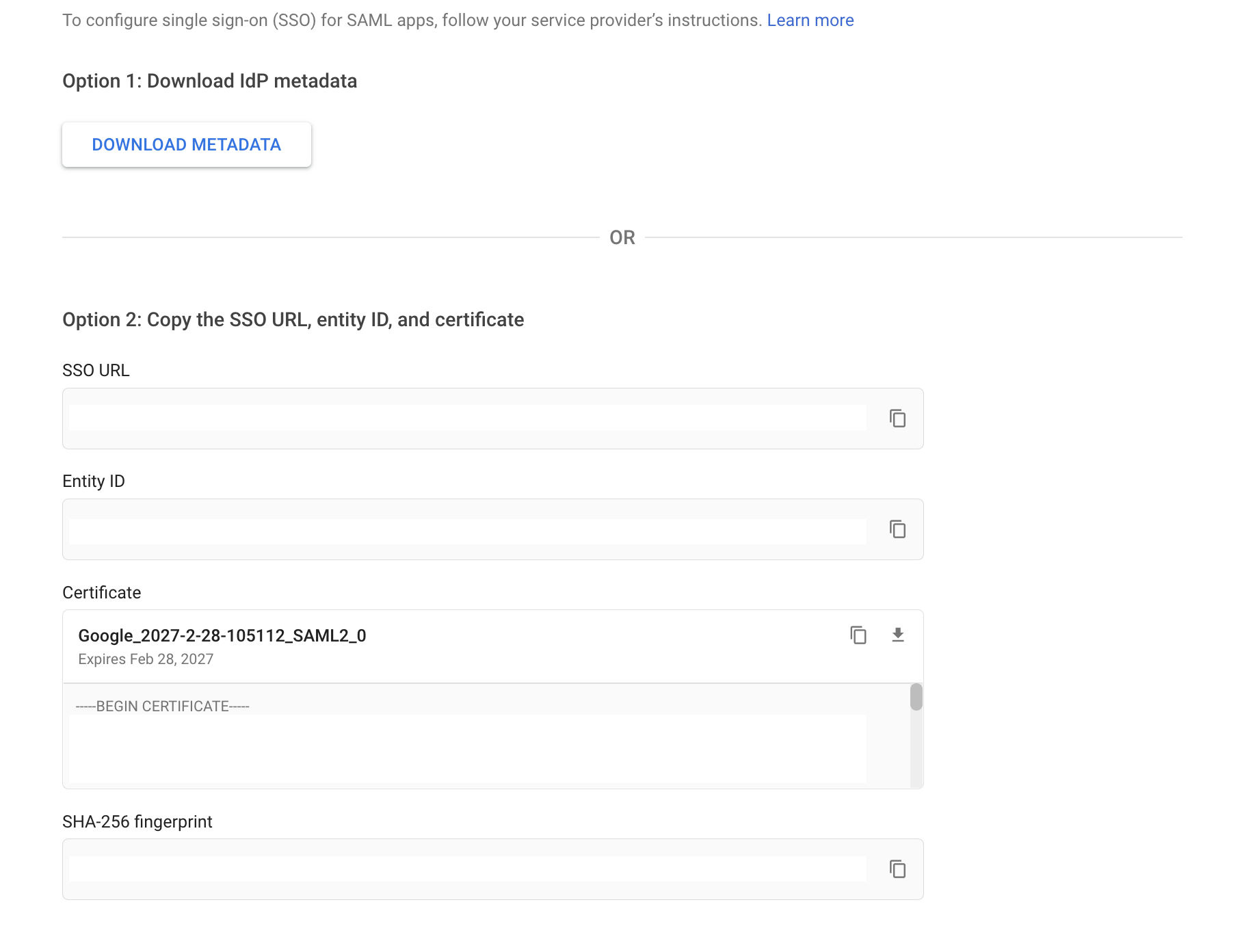
- On the Google Identity Provider details page, use Option 2: Copy the SSO URL, entity ID and certificate. You will need to copy over the SSO URL and Certificate onto Mosaic in Step #7.
Add and Verify Domain on Mosaic
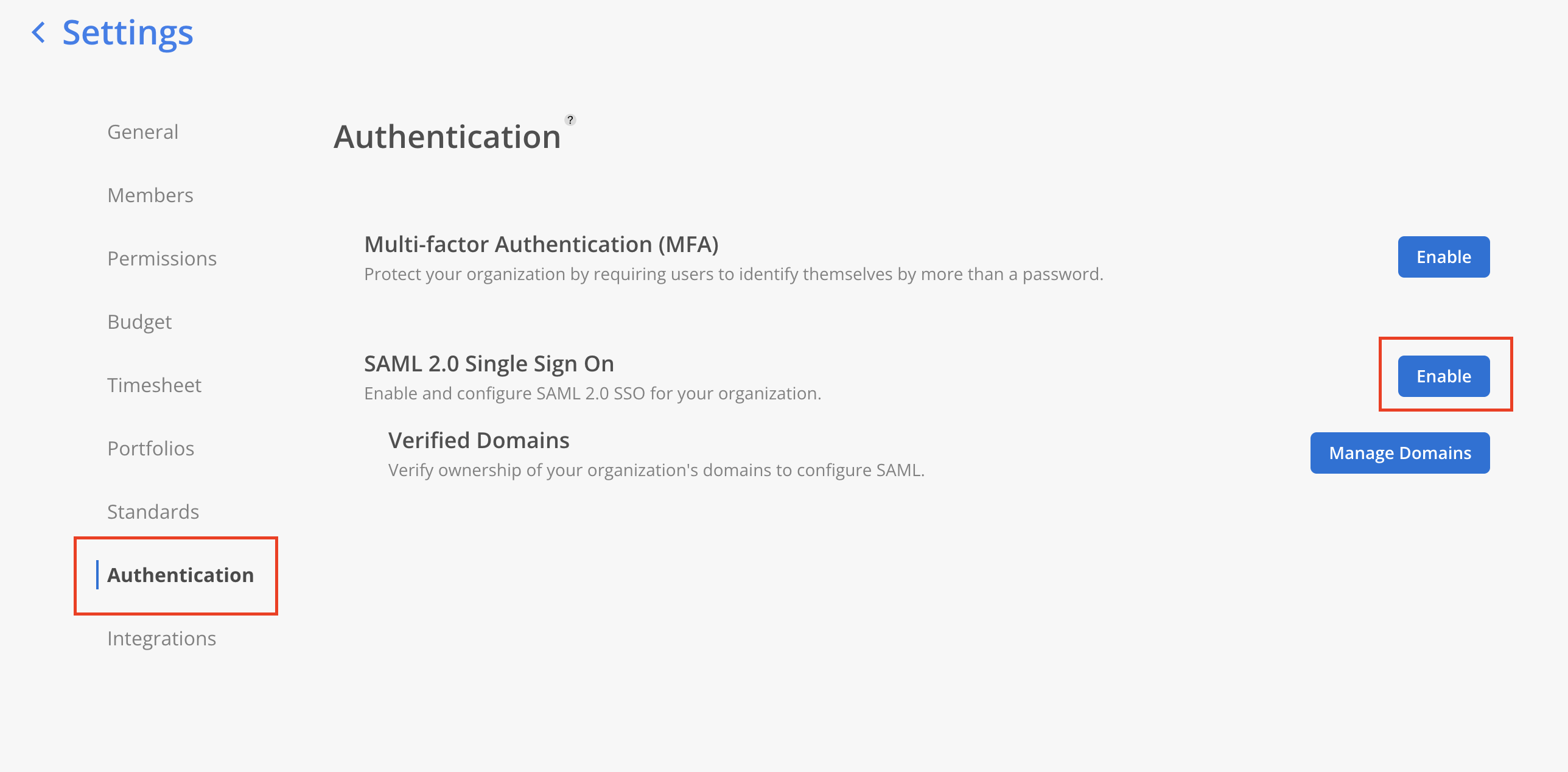
- Go to Mosaic Settings → Authentication page. Under SAML 2.0 Single Sign On, click
Manage Domains.
Please Note:Only admins are able to access the Authentication tab on Mosaic settings.
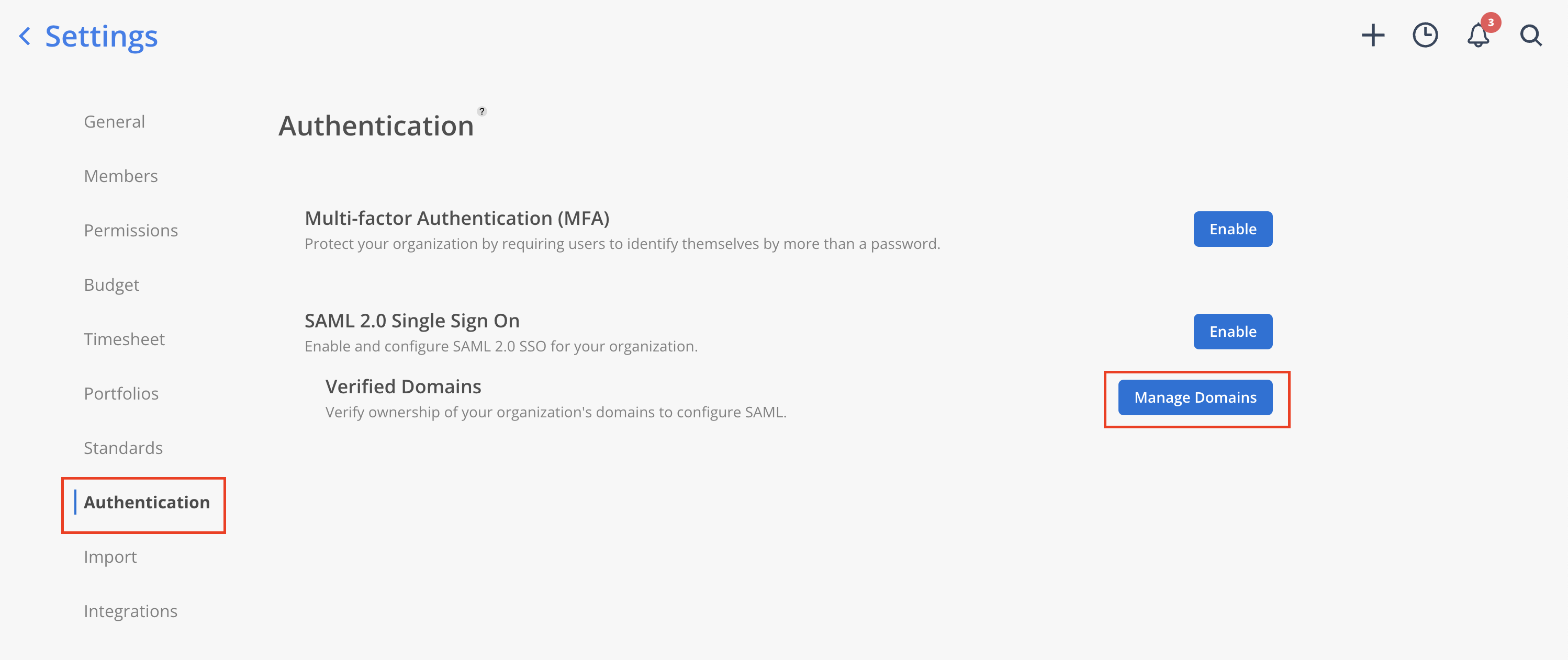
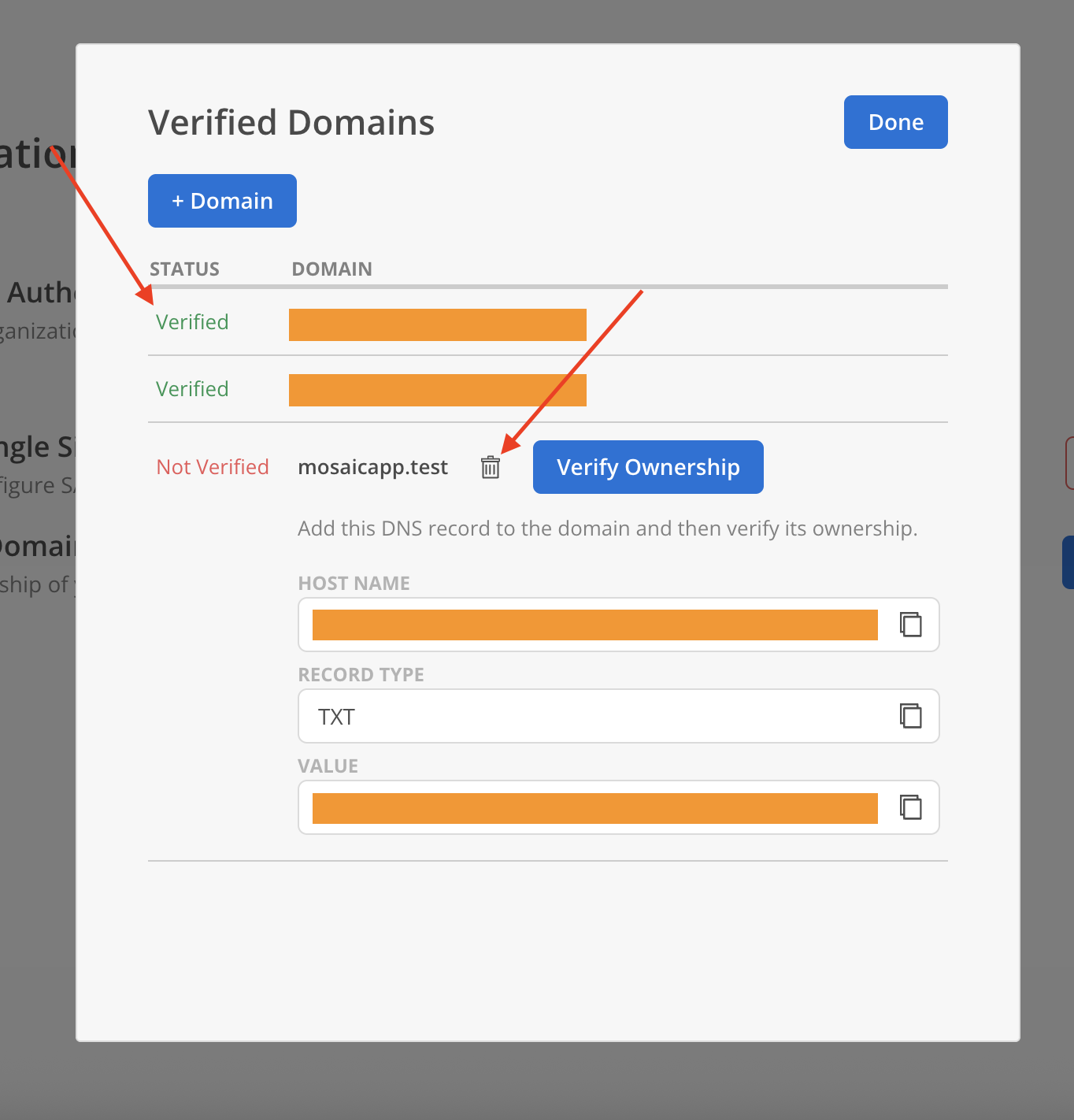
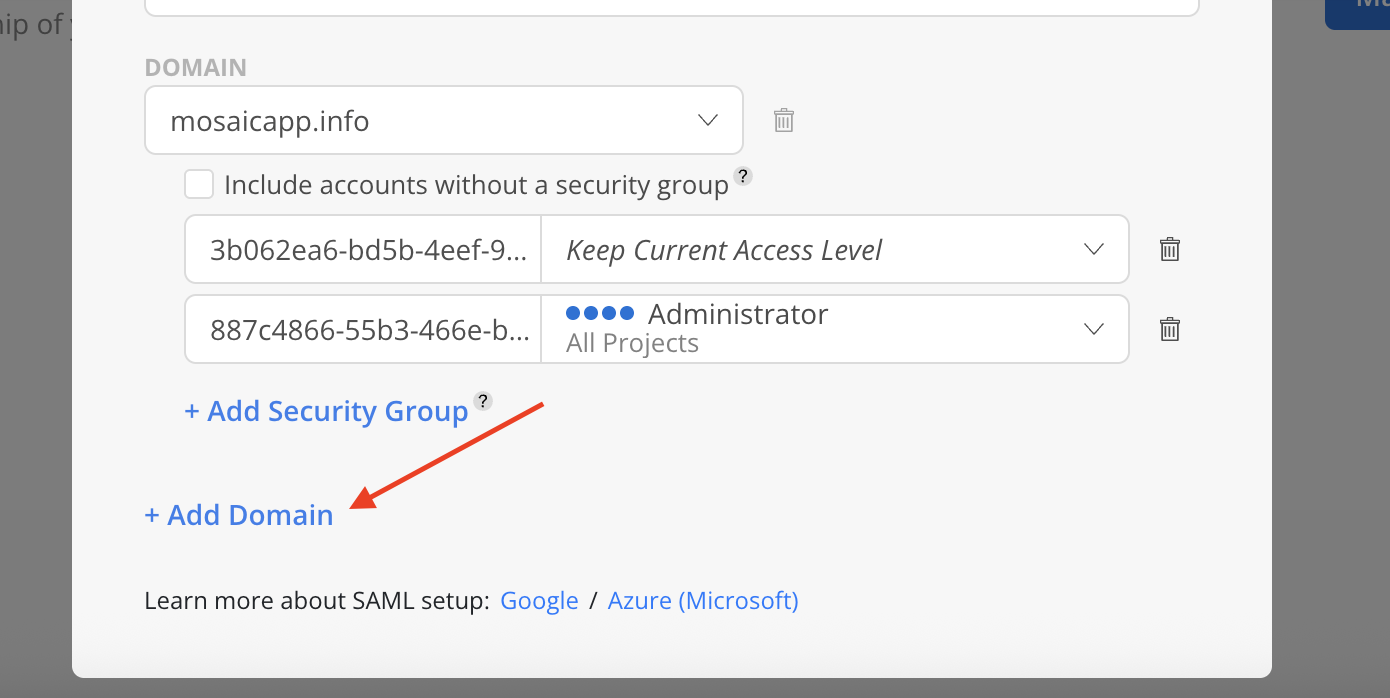
- Select
+ Domainon the Verified Domains Modal.
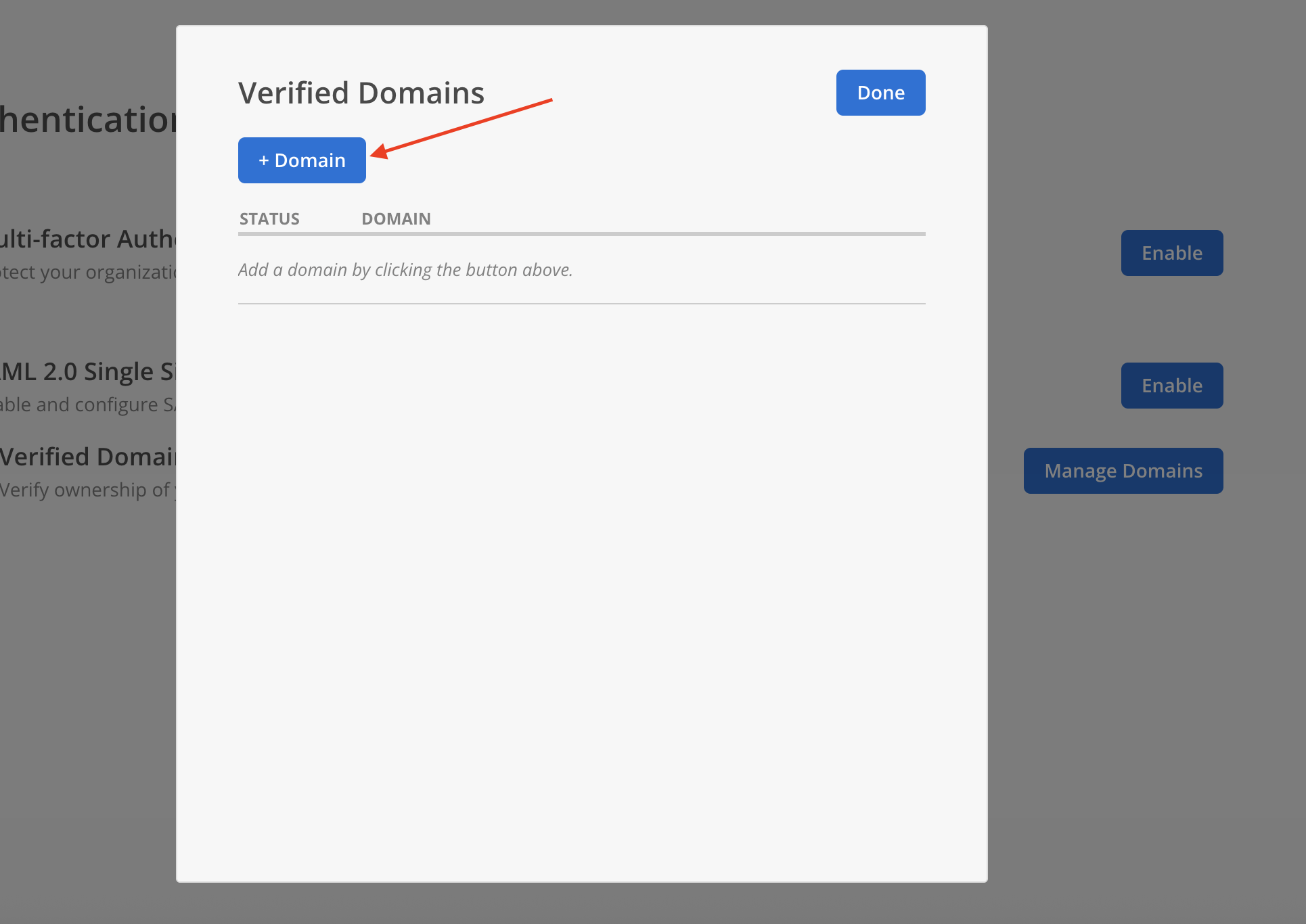
- Enter a your email domain in the host name field. Click
Add Domain.
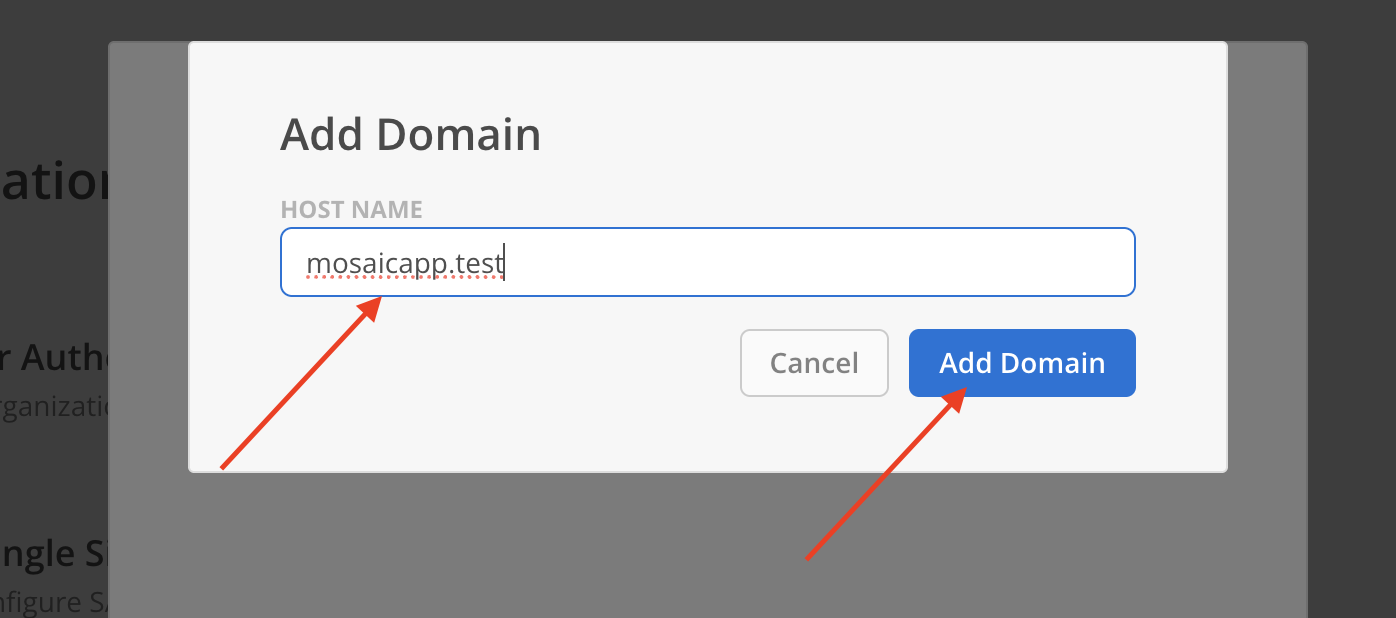
- Newly added domain will appear on the modal with status Not Verified.
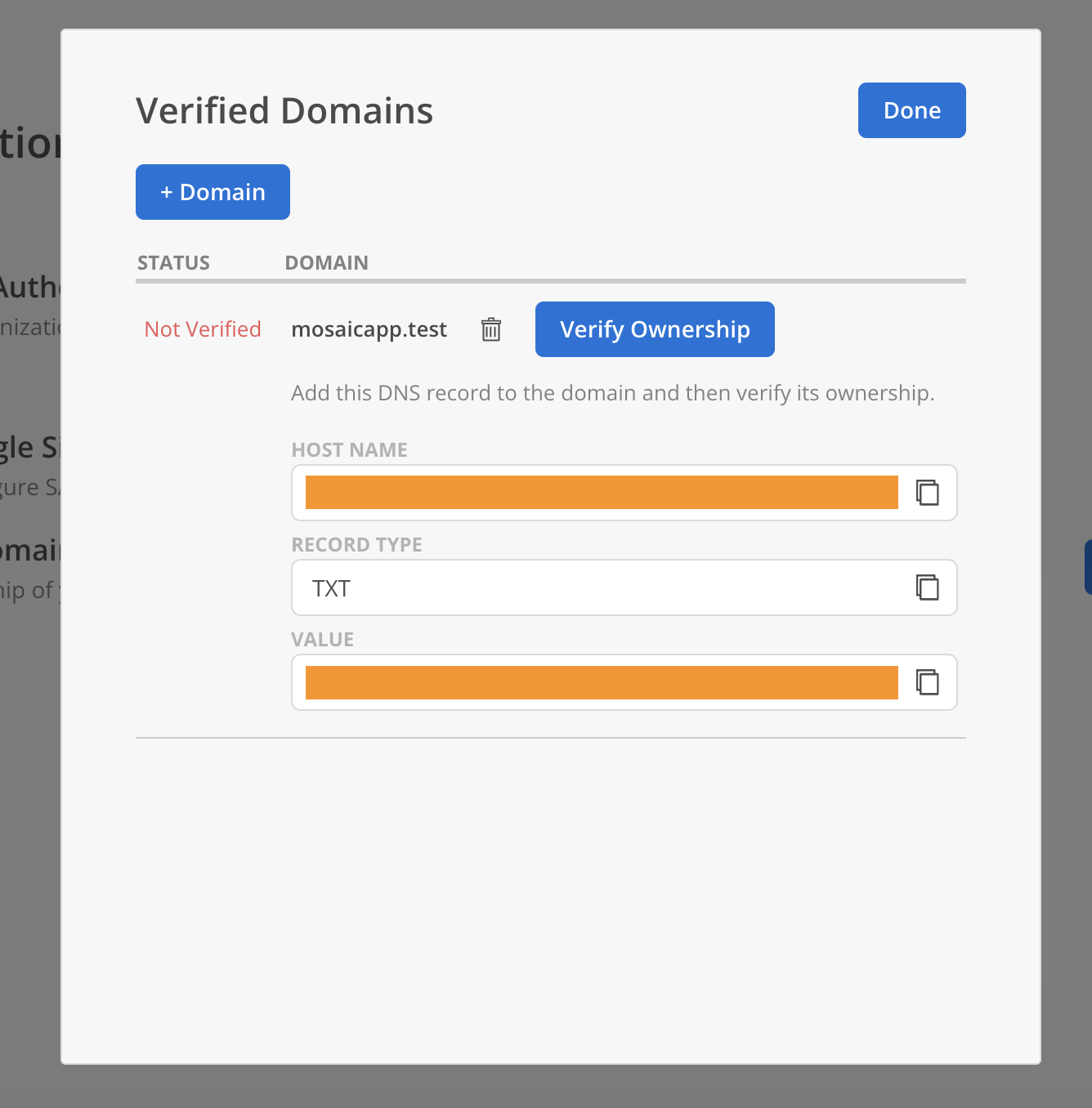
- Share the Hostname, Record Type (TXT), and Record Value with your DevOps team to update the domain’s DNS settings. Click
Verify Ownershipafter completing the DNS configuration.
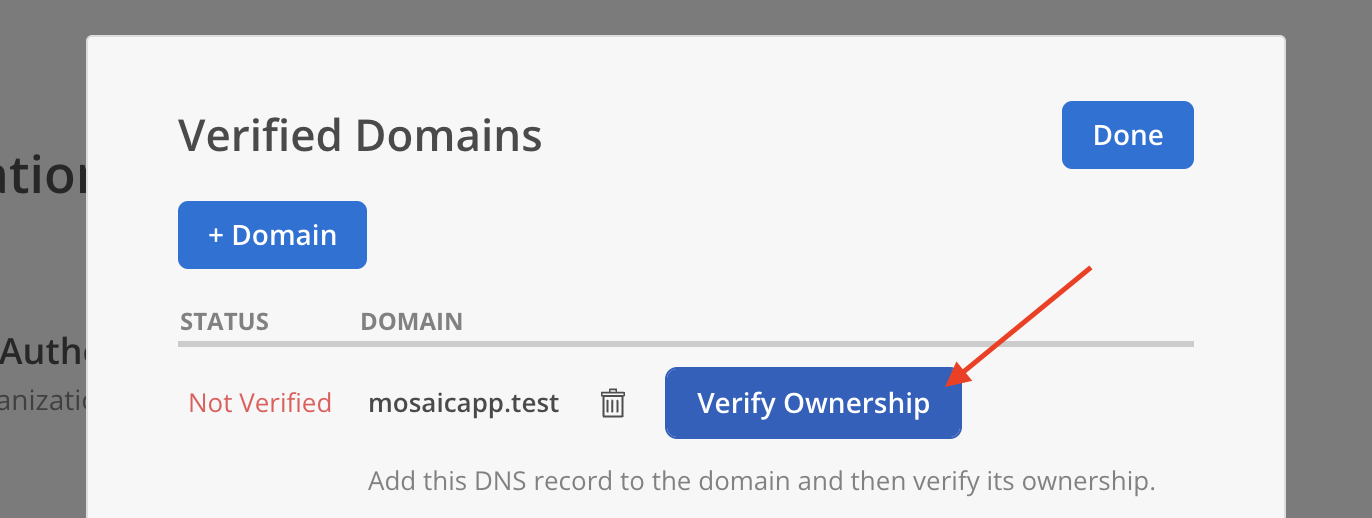
- The domain’s status will update to Verified.
Domains with status Not Verified display a Delete option and can be removed. Once a domain is marked as Verified, the Delete option is no longer available.
Setup SAML
- Click
EnableSAML 2.0 Single Sign On on Authentication page.
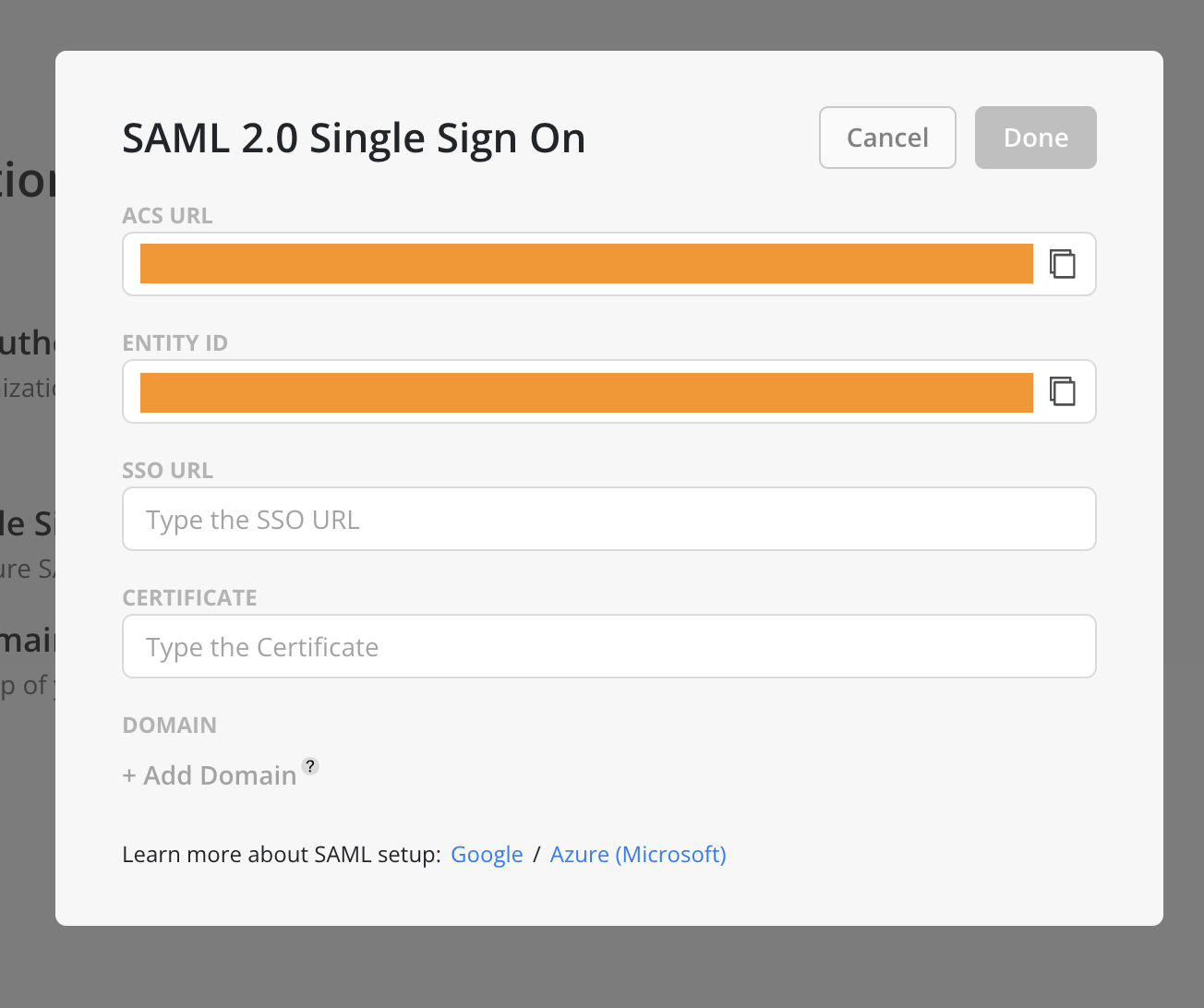
- On Mosaic’s SAML 2.0 Single Sign On menu, fill in:
- SSO URL:
- SSO URL copied from Option 2: Copy the SSO URL and certificate in Step #5.
- Certificate:
- Certificate copied from Option 2: Copy the SSO URL and certificate in Step #5.
Back on the Google Identity Provider details page:
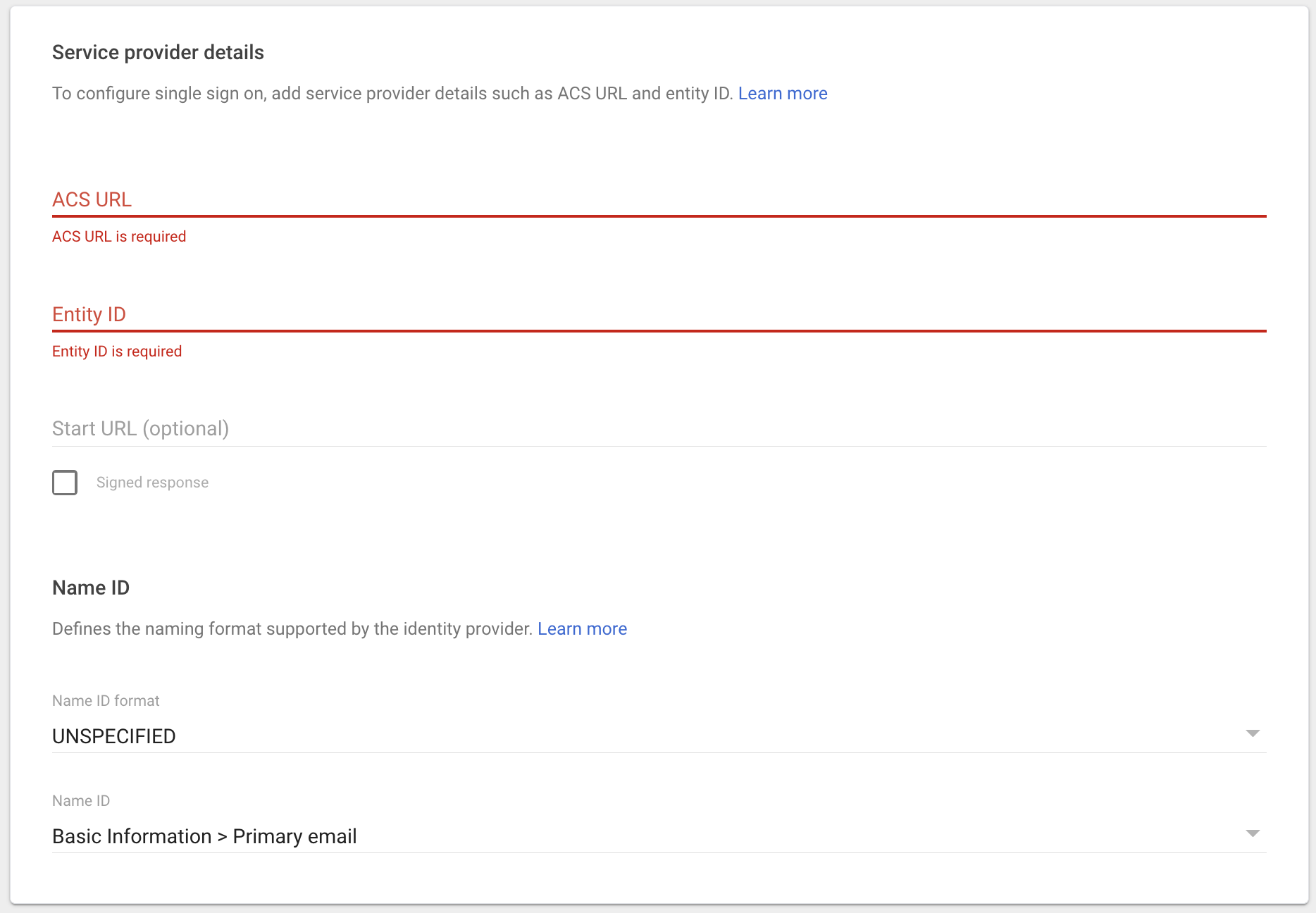
- Copy and paste the ACS URL and Entity ID from Mosaic’s SAML 2.0 Single Sign On menu to Google’s Service provider details section; all other fields can remain untouched.
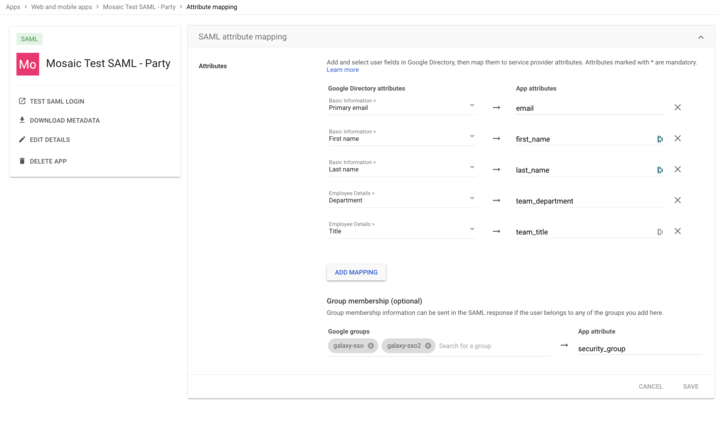
- Next, configure the attribute mapping between Google Directory and App:
- Map the Google Directory attributes to the App attributes as follows:
- Primary email -> email
- First name -> first_name
- Last name -> last_name
- Department -> team_department
- Title -> team_title
- Under Group membership (optional) > Google groups, add the
Groupcreated in Step #1 to the list of Groups. - Under Group membership (optional) > App attribute, enter
security_group. 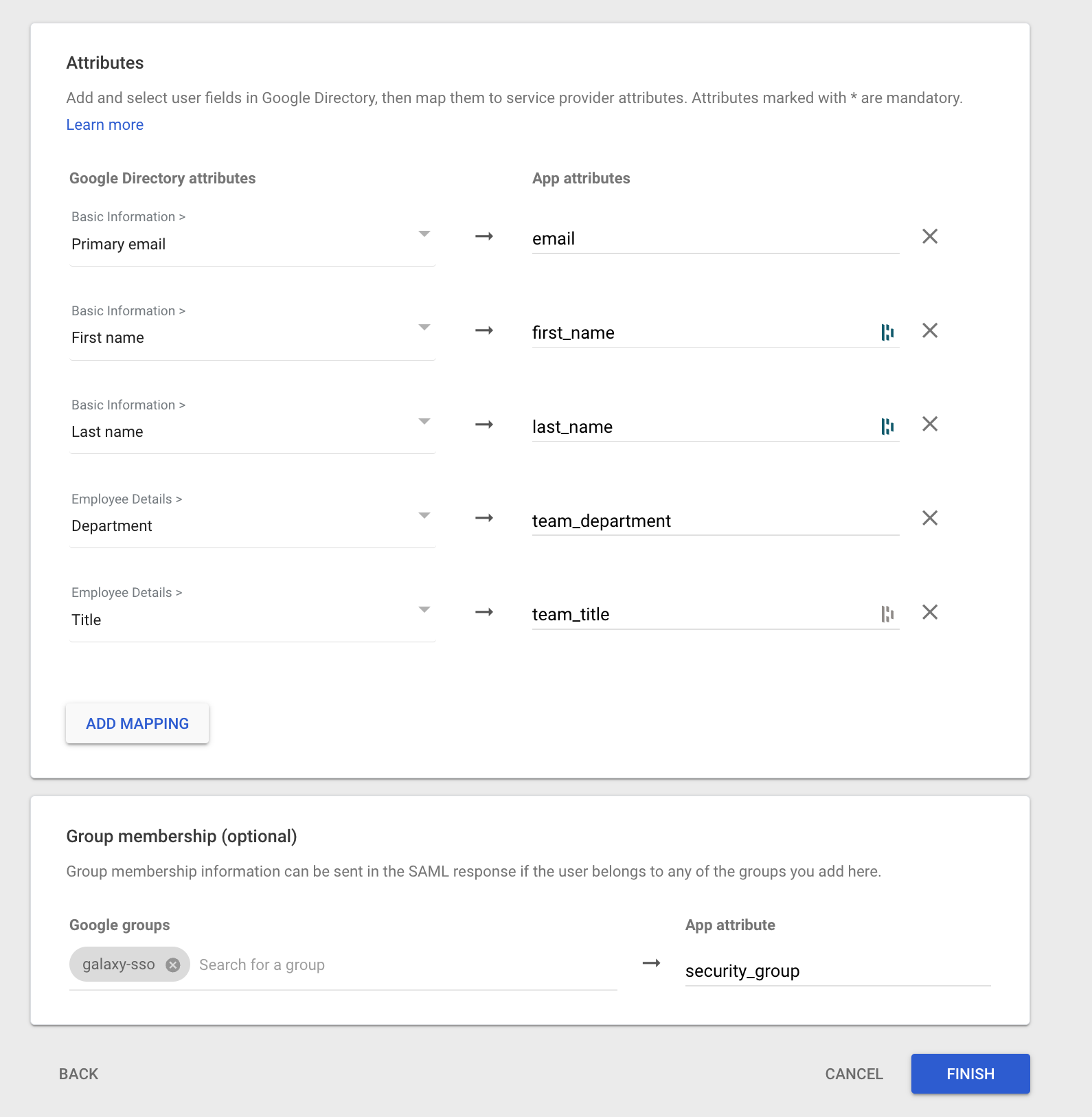
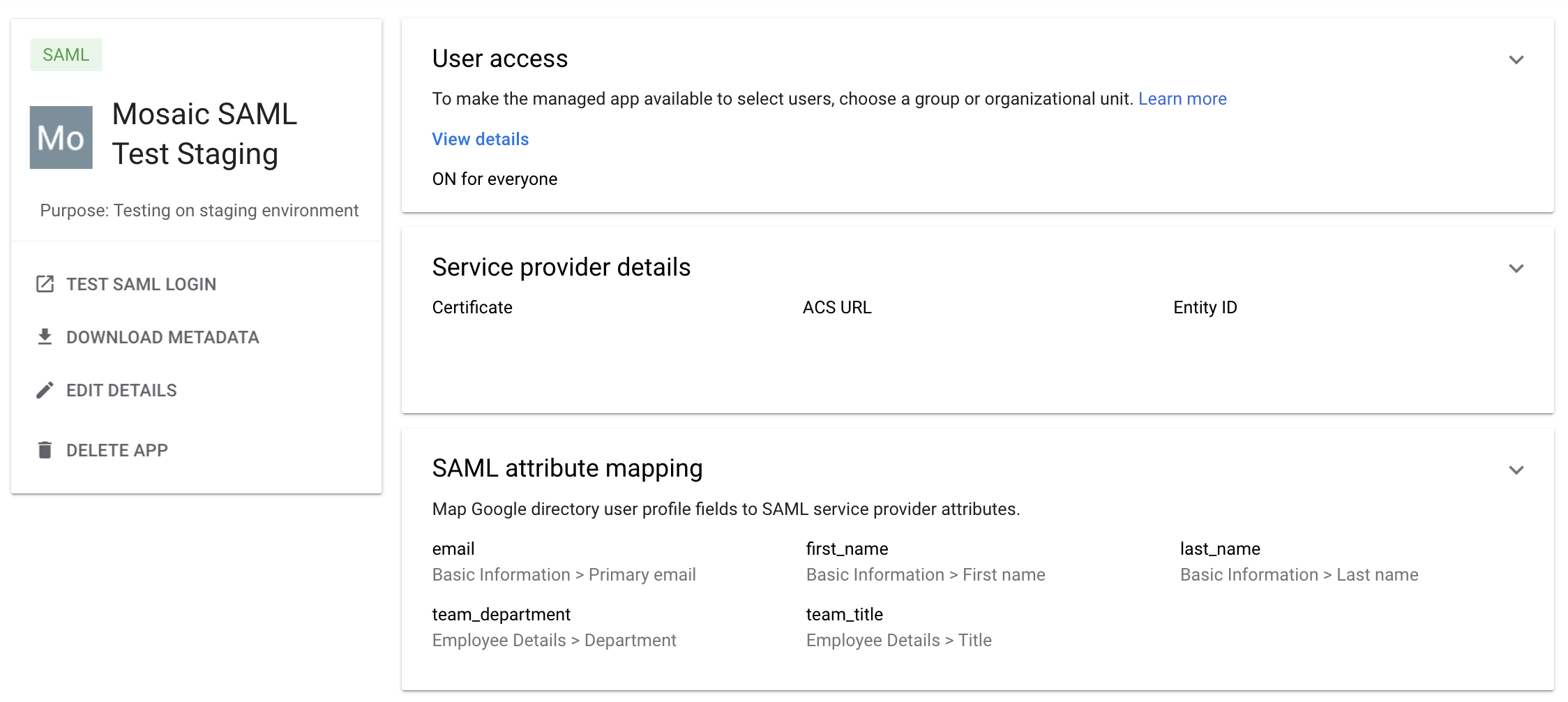
- Upon successful setup, users will be able to see the custom SAML app in Google Workspace’s Web and mobile apps section.

- By default, access to the new custom SAML app is turned OFF for everyone on Google Workspace.
- To make the app available, click on the new custom SAML app.
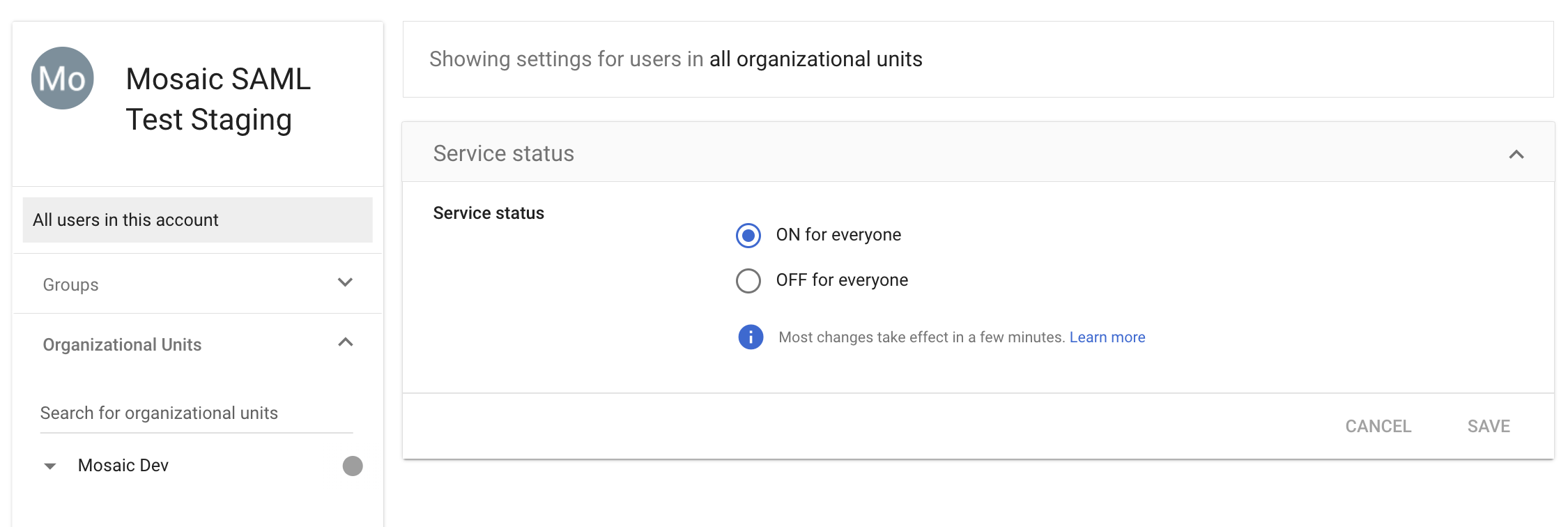
- Click on User access and then click on Groups and select the
Groupyou created. Checking theService Statuson box. Then Save.
Setting up Multiple Teams with SAML:
- To set up multiple teams with SAML simply create another group and add users to that group. (Users can only be in 1 group!)
- When setting up SAML on the new Mosaic team. Skip the step to copy the
ACS URLand theEntity ID.On the SAML app, you will also need to select all groups you want added in the mappings section.
Add Domain and Security Group on Mosaic page
- Click
+Add Domainto select Domain for SAML set up. This will be the Domain associated with Google Workspace. For example,[email protected]has a domain ofthisisdomain.com.
Please Note:The email associated with the admin (who is setting up the SAML) must have the same domain as the one being inputted.
- For example, if the admin uses an email
[email protected], the only domain the admin could input isthisisdomain.com.
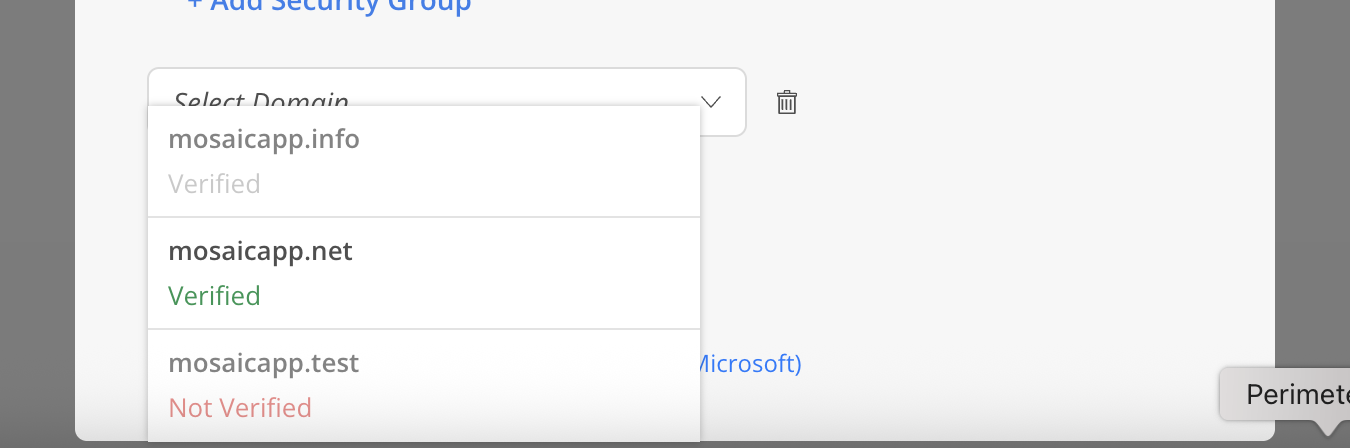
Both Verified and Unverified domains are displayed in the list. However, only Verified domains can be selected. Domains that are already added will appear greyed out.
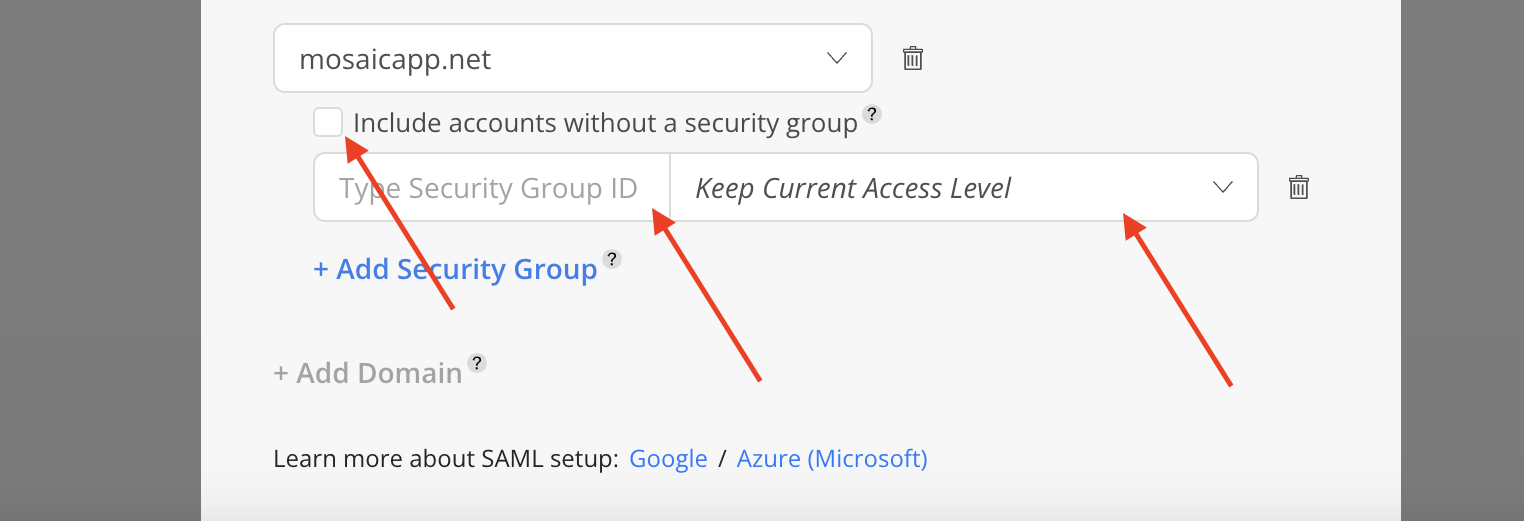
- Configure the Security Group under the domain. Enter the security group name in the security group ID field. Choose the desired access level from the dropdown menu. Optional: Select
Include accounts without a security groupto allow accounts not assigned to any Security Group to log in while retaining their current access level.
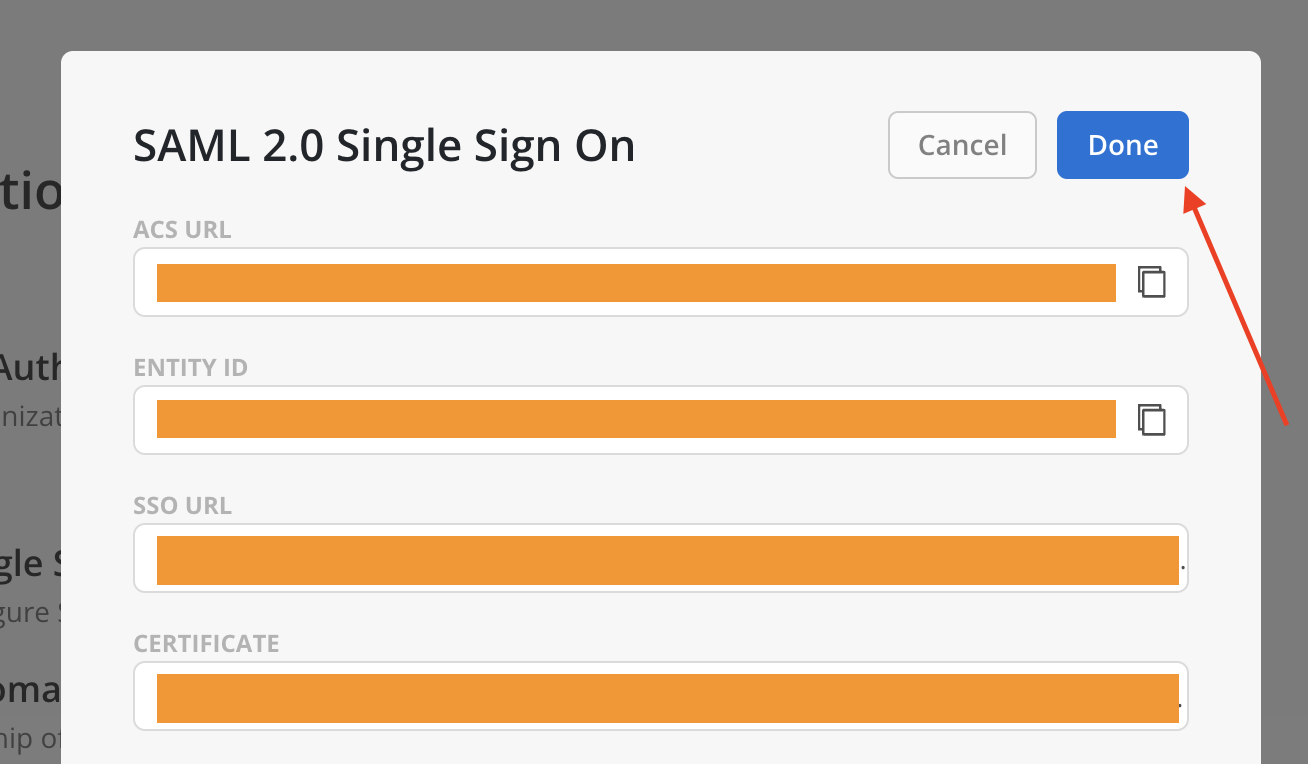
- Click Done on the top once all configuration is completed.
- Upon successful activation, SAML 2.0 Single Sign On will have the following options:

Next time a user with an email address belonging to the specified domain logs into Mosaic, they will be redirected to authenticate with Google the moment they click Next after inputting their email.
Updated 4 months ago